How to Deploy a Cybersecurity Strategy

Just a few years ago, many companies were unprepared for major cyber threats. One of the most notable incidents occurred in 2017 with the WannaCry ransomware attack, which spread rapidly across the globe, exploiting vulnerabilities and holding data hostage. It affected over 200,000 systems across industries using exploits originally developed by the U.S. National Security Agency (NSA).
Not long after, the NotPetya attack hit, wiping data from machines and leaving many organizations ill-prepared despite the recent wake-up call.
Three Methods to Safeguard Technology & Data
Cyberattacks, including phishing, malware, and ransomware, continue to surge in 2024. In fact, according to a recent study by Keeper Security, a staggering 92% of IT leaders report that cyberattacks are occurring more frequently now than in 2023. This increase underscores the growing threat landscape and the urgent need for businesses to strengthen their cybersecurity defenses.
1. Quantify Cyber RiskQuantify Cyber Risk
Translating risk into financial terms can help leadership understand the potential impact. As we’ve seen, cyber threats are only increasing. A 2024 IBM report estimates the average cost of a data breach has now climbed to $4.88 million.
Organizations can no longer afford to take a reactive approach to cybersecurity. Calculating potential losses gives clarity on how much a breach could affect your bottom line and motivates investment in stronger defenses.
2. Align Cyber Risk with Organizational Strategy
A cyber risk management strategy should be integrated with your organization’s overall risk framework. The Institute of Risk Management defines risk appetite as “the amount and type of risk that an organization is willing to take to meet its strategic objectives.” Defining your company’s “risk appetite” ensures your defenses align with strategic objectives.
Regulatory bodies are now pushing businesses to formally establish a cyber risk strategy, which helps management assess whether they are adequately protected from evolving cyber threats.
Approaching cyber risk management in this way allows it to be included in the overall company risk framework, providing insight into whether exposure is affordable or acceptable.
3. Regularly Assess Cyber Defenses and Vendor Risks
Cyber risk assessments must be a continuous process across all departments, including third-party vendors. This includes testing network security, scanning for vulnerabilities, and evaluating the effectiveness of security controls. Third-party risks should be closely monitored as supply chain attacks are becoming more common. Frequent internal and external audits, paired with tabletop exercises, will help your team respond quickly and effectively when an incident occurs.
As described in a “Deploying a Cyber Risk Strategy Guide,” it’s in companies’ interest to carefully monitor their Cyber Risks across departments.
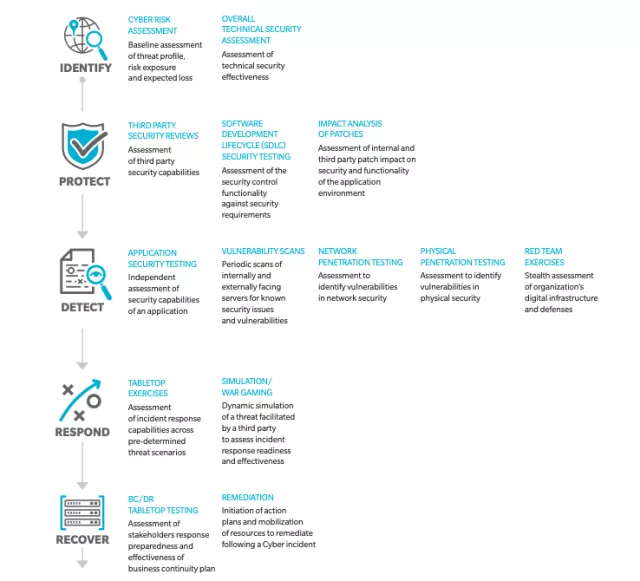
Source: Oliver Wyman
First, identify risks through a cyber risk assessment and an overall security assessment. Secondly, third-party reviews should be conducted; security control functionality should be evaluated against security requirements and internal and third-party impact on security should be assessed. Lastly, evaluate the overall effectiveness of your BCDR plan and how finalized your strategy should remediation efforts be required.
4. Continuously Test Cyber Incident Response
Your incident response plan must be comprehensive and frequently tested to be truly resilient. This involves simulating various attack scenarios, clearly defining departmental roles, and regularly practicing crisis communication protocols. Tabletop exercises help stakeholders understand the nuances of cyber risk and improve their readiness. However, as cyber threats evolve, your plan must be updated and enhanced regularly to ensure it stays effective.
In today’s landscape, cyberattacks are not just an IT problem—they are a business problem. By quantifying risks, aligning cybersecurity with strategy, and rigorously testing response plans, organizations can better defend against potential disruptions and mitigate the severe consequences of a breach.